Problem:
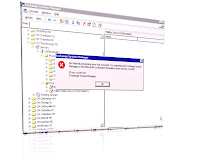
Exchange server 2000 is not accessible. Event ID logs 445; Exchange databases reached the 16 GIG limits. This will cause interruption on the mail flow.
Event Type: Warning |
Event Source: ESE |
Event Category: Space Management |
Event ID: 445 |
Date: 11/27/2007 |
Time: 3:51:57 PM |
User: N/A |
Computer: CHALBIRFS0 |
Description: |
Information Store (5640) The database E:\Exchsrvr\mdbdata\priv1.edb has reached its maximum size of 16383 MB. If the database cannot be restarted, an offline defragmentation may be performed to reduce its size. |
Solution:
I would love to say here, upgrade to exchange 2007 if all it is possible, at least to Exchange 2003 to get the advantage of 75Gig limit in DB. In some cases, decision makers (Managers) are very none sense, to be honest. I have seen million of times so far same scenario. For technical people it is very frustrating to deal with manager who has no clue about current technology. Remember this is the way it is and we have to leave with this. Follow the step below
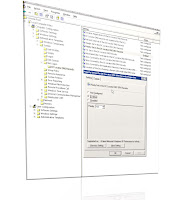
ESEUTIL /D is the immediate action we have to take in this particular issue. We bumped the DB size to 17GIG with following registry hack.
Right click, new Dword Value, and name it "Temporary DB Size Limit" and enter value 1.Restart information store service for changes to take effect. Requires Service Pack 3 for Exchange 2000 and the following registry entry:
The C drive was out of space therefore we need to perform the Defrag to E drive, where we had plenty of free space
C:\>"C:\Program Files\Exchsrvr\BIN\ESEUTIL.EXE" -d "E:\Program Files\Exchsrvr\MD BData\priv1.edb" /te:\temp.edb
This was the Temp file is going to be created on the E Drive. Many o f you know if already the story behind the temp database. Exchange will create an empty database in this example is the Temp database and will copy good mail data into this DB. When exchange is done, it will tell you "Hey I have created brad new database, go ahead delete the original one and use this one instead."
Determine White Space Event id 1221. If it is too late and exchange databases are dismounted due to space problem, use ESEUTIL /MS determine the white space.
Space Dump with ESEUTIL /MS to determine the space. Also ensure that you have 110% free disk space associated with the Exchange database size.
You can check the integrity of your Exchange database with ESEUTIL /G
After running ESEUTIL, check the log file called "integ.raw "to see the results.
Let's talk about ISINTEG in general (Isinteg -fix -test alltests)
ISINTEG is the only repair utility that understands the Exchange database as an Exchange database (taken from MS support)
- Isinteg understands the relationships between those tables and records that turn them into folders and messages.
- At the end of an Isinteg fix run, you will likely see hundreds to thousands of warnings, no worries, but we need to worry if there is even one error, and rerun the Isinteg until there is no more errors are being reported.
- Before you do this make sure,
- The information store service is running
- The mailbox store is dismounted
- Isinteg -ServerName –Fix –Test alltests
Here are the final Steps:
- Run ESEUTIL /MS (determine the space, you won't be blind)
- Run Eseutil /P ( Hard Repair)
Run Eseutil /D. ( Defrag)
RUN Isinteg -fix -test alltests (fixes the logical problems)
Example: isinteg -pri -fix -test alltests
Best,
Oz ozugurlu